Last week, the so-called WannaCry ransomware virus began infecting computers. It quickly spread to 150 countries, infected over 230,000 computers and disrupted critical networks like hospitals and transportation systems. WannaCry may be the biggest, and most expensive, worldwide ransomware attack to date.
WannaCry is just one variation of ransomware. There was an increase of 752% in the number of ransomware types, or families, in 2016. Millions of users, big institutions and individuals, have been and will be, victims.
You are at risk, but far from helpless to defend yourself against becoming a victim. Read on to learn what to look for, and what steps you can take to make yourself a very hard target.
What is ransomware?
Ransomware is a type of malware (malicious software) that, once on your computer, encrypts your data and makes your computer useless. If your computer becomes infected, you will have to pay the hacker a “ransom” to unlock your data—or lose your data forever.
How does ransomware get onto a computer?
The most common way ransomware is introduced to a computer (the “top infection vector” in techie terms) is via spam email. A victim opens a seemingly innocent email that contains a link that, when clicked, activates a virus (malicious software.) The virus self-installs on the new host computer and takes over, encrypting data, files, pictures—everything. The infected computer is rendered useless.
Not all viruses require user interaction, however. It appears that WannaCry may have exploited a vulnerability in Windows—for users who failed to install updates or were running old Windows versions, like Windows XP. This is an important message: always update your system, apps, and anti-virus software to block new and emerging threats!
A computer infected with ransomware will display a message with instructions on how to pay the ransom. The ransom is usually demanded in Bitcoin, an untraceable Internet currency.
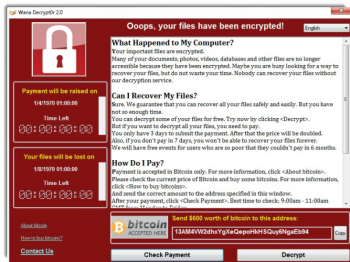
The process to create a Bitcoin account is a complicated and time-consuming process. There are so many ransomware infections that some hackers actually have links to tutorials and staff live chat rooms to help their victims comply with payment demands.
How do cybercriminals trick victims into installing a virus?
Hackers use social engineering to urge victims into taking an action, like clicking a link or visiting a website. Social engineering is the use of psychological techniques to instill a sense of urgency, appear as a normal request or mimic an important or urgent official notice.
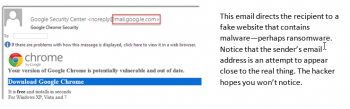
Hackers pose as acquaintances and coworkers. They send emails, even text messages, that appear to be from banks, businesses and even the government. Hackers use urgency and fear to get victims to take actions they might otherwise not.
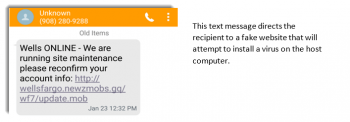
Phishing for information using fraudulent text messages is called SMiShing. SMiShing is a growing threat.
Who spreads ransomware?
Hackers seeking to profit from ransomware range from teens in Malaysia to corrupt nation-states like North Korea. Hacking kits are sold on the Internet, enabling anyone, even without coding knowledge, to set up a ransomware site.
Once released and “in the wild”, ransomware is often spread by people who unknowingly forward infected email. We trust email we get from friends, coworkers and family, making this an effective way to spread malware. Some email viruses are just cute pictures that we share with others, completely unaware that the pictures, or sales coupons or a million other variations, are actually links to viruses, infected websites and malware.
Am I powerless to protect myself?
Absolutely not. You have the power to protect yourself from almost all attacks.
Hackers rely on several layers of vulnerability. Some attacks scan the Internet looking for computers with unpatched vulnerabilities and out-of-date software. The vast majority of attacks, however, require user interaction. Hackers need you to click on a link or open an attachment to begin the process of infection. Here are the most important steps you can, and should, take to avoid viruses:
- Update your devices with the latest software and patches. All devices, from computers to smartphones, need to have the latest security patches installed to be safe.
- Email can be “spoofed” to hide the actual sender and appear as someone else. Carefully check the sender’s email. You may need to hover over the sender’s address and wait for the popup box with the actual address. (Some email readers won’t display the actual sender).
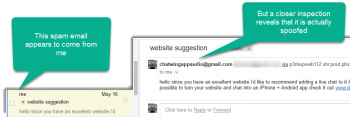
- Don’t click on links or open attachments to email you aren’t expecting or if you don’t know the sender.
- Never run programs or executable files (files with a “.exe” suffix) from sources you do not know are legitimate.
- Verify email requests for information, even from sources that seem legitimate.
- Install a powerful anti-virus program, like Norton Anti-virus. You can buy multiple licenses on Amazon for your entire household.
- Update old unsupported operating systems like Windows XP.
- Be suspicious of all urgent messages that require you to take some immediate action. Hackers pose as banks, the IRS, the postal service, the FBI…
Backup your data
Backup your files and pictures up to a separate computer, the cloud or a dedicated backup device. If you are hacked, you can start over with a clean installation of Windows (or whatever operating system) without losing anything of value—besides time and aggravation. You can back up unlimited photos to Google. Microsoft’s OneDrive, Google Docs, Dropbox, and a host of other services offer a limited amount of free storage and options to purchase more. Here’s a bonus: most of these integrate so well with your computer (as well as smartphones and tablets) that the backup is completely automatic and invisible to you.
Cybercrime, including exploits of ransomware viruses, will continue to grow. But you can truly minimize your chances of becoming a victim by being aware, updating your computer and apps, and running an effective anti-virus program.
Save






Leave A Comment
You must be logged in to post a comment.